In early August, Wired reporter Mat Honan had his most precious passwords hacked via a complex series of social engineering exploits. The breach made headlines because it exposed security flaws in Apple and Amazon customer service policies; but let's not forget that the Honan saga capped a long summer full of server invasions that exposed millions of user passwords en masse.
In June, hackers stole some 6.5 million LinkedIn passwords and posted them online. That same month, intruders compromised about 1.5 million eHarmony passwords in a security breach, and in July hackers grabbed 450,000 Yahoo Voice passwords. Among the most common passwords used by those Yahoo members: "123456," "welcome," and the ever-popular "password."
The fundamental problem isn't that these sites should have done a better job protecting user data (though they should have). And it isn't that users chose passwords that were exceedingly easy to crack and then recycled the same flimsy passwords at every site where they registered (though they did).
The problem is that passwords have become self-defeating, often impotent tools in the grand scheme of digital security. We need too many of them, and the strong ones are too hard to remember.

"To use the Net these days you have to have dozens of passwords and logins," says Terry Hartman, vice president of global security solutions for Unisys. "Every time you go back to a site, it feels like they've introduced new rules to make passwords more complex. Eventually, users revert to using one password for everything."
In short: The password system is broken. All of the passwords breached in the LinkedIn, eHarmony, and Yahoo exploits had been "hashed"—that is, the actual passwords had been replaced with algorithmically generated code. This transforms the passwords stored on servers (and stolen by hackers) into alphanumeric gobbledygook. Still, if your password is as simple as, say, "officepc," a hacker can easily crack it even in hashed form by using brute force or a rainbow table.
But all is not lost. Complex passwords infused with numbers and special characters (and bearing no resemblance to a real name or word) give you a fighting chance against hackers, and you can store these codes in a handy password management app. Websites, meanwhile, are doing more to beef up security at their end, requiring multifactor authentication, and it looks as though biometric technology will soon be employed for mass-market security as well.
The password problem won't go away any time soon, however, and for now we'll have to rely on the applications, services, and emerging technologies explained below to stay one step ahead of the bad guys.
Password vaults
Password management programs are like spam filters—boring but essential tools for managing your digital life. A good password manager remembers all of your logins, replaces the simple passwords you choose with complex ones, and lets you change those passwords quickly if a site or service you use gets hacked.

The best part: Instead of having to remember dozens of unique passwords, you only have to remember one: the master password for your vault. And unless you always log on from the same machine and the same browser (in which case you're probably reading this on an AOL dialup connection), you'll want a cloud-based program like LastPass, 1Password, or Roboform that can apply your logins to any PC, phone, or tablet you use.
The downside: You still have to remember your master password, and it really should be a good one, packed with a mixture of numbers, capital and lowercase letters, and special characters such as question marks and exclamation points.
Of course, an attacker who manages to plant a keylogger in your system will be able to sniff out your password as you type it, notes Robert Siciliano, an online security expert for McAfee who uses a password vault to store more than 700 logins. Similarly, if crooks hack a cloud-based password vault—as happened to LastPass in May 2011—it could be game over. Fortunately for LastPass customers, no sensitive information was breached in the 2011 attack; but the next time a successful intrusion occurs (and that it will happen to some security firm somewhere is inevitable), users might not be so lucky.
Bottom line: Password management vaults offer immense value, and are essential tools for anyone who values digital security.
Multifactor authentication
Complex passwords stored in an encrypted vault are only a first step. Some sites rely on a second level of security to identify users—typically a piece of hardware that only the rightful user has access to. That way, even an attacker who knows your password will need access to, say, your phone or computer in order to steal your data.
Financial institutions are required by law to use multiple factors when handling online transactions, but they may do it in the background by authenticating your machine or its location, says Siciliano. So, for example, if you live in San Francisco and someone in Shanghai attempts to access your bank account, that transaction may be blocked, or that person may be required to provide an additional piece of authentication by entering a number sent to a device provided by the bank.
Google and Facebook now offer two-factor authentication as well: You can have them send a temporary PIN to your cell phone whenever you log in from an unfamiliar machine (this PIN must be provided along with your password the first time you attempt to log in via that new machine). This failsafe would have prevented all the hardship Mat Honan suffered last month.
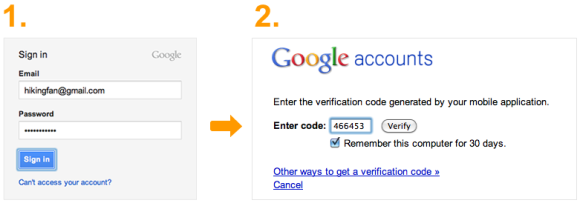 Google's two-part authentication system ensures a greater level of security, but many users find it tiresome in real-world practice.
Google's two-part authentication system ensures a greater level of security, but many users find it tiresome in real-world practice. Unfortunately, though, aside from banks and a handful of high-profile websites, most places online simply don't offer multifactor authentication—in part because it's not very convenient, and the vast majority of Internet users are willing to trade security for hassle-free logins.
"Two-factor authentication doesn't always pass the grandma test," says Siciliano. "That means more support calls, more password resets, and higher costs. That's why it's typically only used by companies with a lot to lose."
Biometrics
The beauty of biometrics is that you don't have to remember anything at all, much less a complex password. Instead, a biometric security system taps into the unique properties of your own physical packaging to authenticate your identity.
Biometric systems can scan fingerprints, irises, faces, and even voices to establish whether a person should have access to a service or piece of hardware. They're not yet deployed for the major cloud services, but Terry Hartman of Unisys says major banks are piloting biometric identification systems now, and expects them to begin rolling out next year. Apple's recent $360 million acquisition of AuthenTec, maker of fingerprint-scanning technology, suggests that some form of biometric identification may be built into future Apple products.
 Rudimentary biometric security is already available on many notebooks.
Rudimentary biometric security is already available on many notebooks. Biometrics aren't perfect, however. Researchers have gamed fingerprint scanners by using gelatin fingers, and they've fooled facial recognition systems by using photographs. At last July's BlackHat conference, security researchers demonstrated a way to trick iris scanners by reverse-engineering the image data.
And of course, hackers can target biometric data stored in a central database, and steal identities by substituting their own biometric data in place of their victims'. As with passwords and other personally identifiable information, the level of protection provided by biometric security would depend entirely on the competence of whoever stored the data (we all know how well that worked at LinkedIn).
Requiring biometrics at login could also make anonymity difficult (if not impossible) for political dissidents, whistleblowers, and people who inhabit multiple identities for personal or professional reasons. Fears over Minority Report-style government surveillance may also give many consumers pause.
Despite all this, Joseph Pritikin, director of product marketing at AOptix Technologies, a maker of iris scanners deployed at airports and border crossings, predicts that smartphones employing biometrics will be one of the key identification devices of the future, in part because the data can be stored securely on the device itself.
"It will be a combination of something I am and something I have, most likely a smartphone," Pritikin says. "Their hardware-based encryption would be difficult to compromise."
One ID to rule them all
Ultimately, the ideal solution for password fatigue is to unify all of our disparate logins and online identities. Enter the Obama Administration, which in April 2011 launched a public-private initiative, the National Strategy for Trusted Identities in Cyberspace, to develop an identity ecosystem that would allow consumers to use any verification system and have it work seamlessly across any site.
Such a system would be able to verify that you're old enough to buy wine online or that you qualify for a student discount, without necessarily sharing all of your personal information with each site, says Jim Fenton, chief security specialist for OneID, an Internet identity management system. The system would also allow you to operate under a pseudonym, if that's how you wanted to roll.
But the wheels of government churn slowly. Last month, the NTSIC's steering committee held its first meeting. Among the issues it will eventually have to tackle are how much information should be shared between parties, and how much control consumers should have over that information, says Fenton, a member of the steering committee's privacy group.
In other words: Help is on the way, but it won't get here soon. In the meantime, we're stuck with passwords. Create some good ones, and make sure they're under lock and key.
19 Sep, 2012
-
Source: http://www.pcworld.com/article/2010058/password-management-future-technology.html
--
Manage subscription | Powered by rssforward.com
Anda sedang membaca artikel tentang
How to find happiness in a world of password madness
Dengan url
http://bakterimakanan.blogspot.com/2012/09/how-to-find-happiness-in-world-of.html
Anda boleh menyebar luaskannya atau mengcopy paste-nya
How to find happiness in a world of password madness
namun jangan lupa untuk meletakkan link
How to find happiness in a world of password madness
sebagai sumbernya
0 komentar:
Posting Komentar